Detecting rip-off emails is getting more and more tough as attackers use increasingly more refined strategies. A brand new report highlights a way which makes pretend security alerts from Google and PayPal look extraordinarily convincing.
It reinforces the necessity to apply a easy however efficient safeguard anytime you obtain what appears to be an essential e mail requiring your speedy consideration …
How do phishing assaults work?
A phishing assault is when somebody sends you a pretend e mail claiming to be from an organization or group, and together with a hyperlink asking you to login to take some motion. Fairly often the e-mail will create a way of urgency, for instance claiming that your account has been compromised.
The hyperlink will take you to a webpage meant to appear to be the true factor, however which is used to gather your login credentials.
There are a variety of steps corporations like Apple and Google take to attempt to detect and block phishing assaults, in addition to clues you’ll be able to search for to establish many fakes. Nonetheless, Bleeping Computer studies on a intelligent technique getting used to impersonate Google and PayPal.
A extremely convincing assault technique
A extremely skilled developer and safety skilled obtained considered one of them, and did some digging.
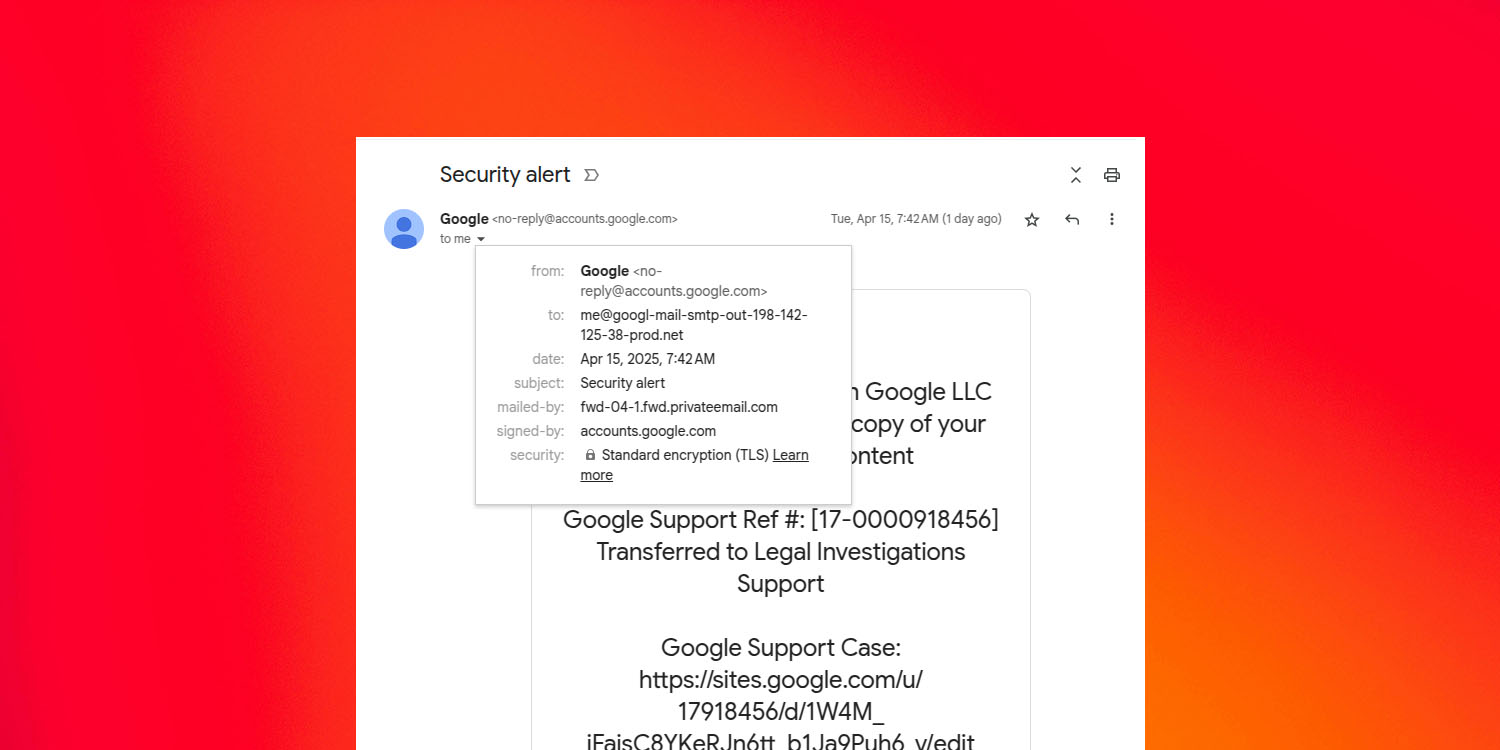
Nick Johnson, the lead developer of the Ethereum Title Service (ENS), obtained a safety alert that gave the impression to be from Google, informing him of a subpoena from a regulation enforcement authority asking for his Google Account content material.
Virtually every little thing regarded reputable and Google even positioned it with different reputable safety alerts [and] the message was signed and delivered by Google.
What the attacker had accomplished was create the pretend login web page on websites․google․com, a website hosting service anybody can use. In addition they used a trick to get Google to ship them an actual e mail, then forwarded it with the rip-off content material.
This meant it appeared to have handed the usual safety checks meant to establish this kind of rip-off.
The fraudulent message appeared to return from “no-reply@google.com” and handed the DomainKeys Recognized Mail (DKIM) authentication technique however the true sender was completely different […]
“Since Google generated the [original] e mail, it’s signed with a legitimate DKIM key and passes all of the checks,” Johnson says, including that the final step was to ahead the safety alert to victims.
The weak spot in Google’s programs is that DKIM checks solely the message and the headers, with out the envelope. Thus, the pretend e mail passes signature validation and seems reputable within the recipient’s inbox.
Moreover, by naming the fraudulent deal with me@, Gmail will present the message as if it was delivered to the sufferer’s e mail deal with.
The login web page can also be a precise copy of the true factor. Google says it’s engaged on a repair to stop this technique being utilized in future, nevertheless it stays attainable for now.
An identical technique has been used with PayPal, by which a present characteristic was used to have the phishing e mail seem to originate from a real PayPal deal with.
Learn how to defend your self
An important step you’ll be able to take is to by no means click on on hyperlinks obtained in e mail, even when it seems real. As an alternative, use your personal bookmarks or sort a identified real URL.
Be particularly cautious of emails which indicate urgency. Frequent examples embody:
- Claiming that your account has been compromised
- Sending you an bill for a pretend transaction, and a hyperlink to cancel it
- Claiming you owe cash for tax, highway tolls, and so on, and have to pay instantly
Within the Google case, it claims regulation enforcement has served them with a subpoena requiring entry to your account content material, and alluring you to object.
Highlighted equipment
Picture: 9to5Mac collage of screengrab from Nick Johnson on background by Mathias Reding on Unsplash
FTC: We use revenue incomes auto affiliate hyperlinks. More.



 Viesearch - The Human-curated Search Engine
Blogarama - Blog Directory
Web Directory gma
Directory Master
http://tech.ellysdirectory.com
8e3055d3-6131-49a1-9717-82ccecc4bb7a
Viesearch - The Human-curated Search Engine
Blogarama - Blog Directory
Web Directory gma
Directory Master
http://tech.ellysdirectory.com
8e3055d3-6131-49a1-9717-82ccecc4bb7a